Mastering Compliance Frameworks: GDPR, HIPAA, and SOC 2 Using Azure Security and Compliance Services

Navigating Compliance Frameworks with Azure Security and Compliance Capabilities
In today’s hyper-connected world, regulatory compliance is no longer optional; it’s a critical pillar of trust, security, and operational success.
With rising global regulations like GDPR, HIPAA, and SOC 2, organizations face mounting pressure to safeguard sensitive data, avoid penalties, and maintain customer confidence.
Microsoft Azure’s security and compliance ecosystem offers a robust solution to meet these demands head-on. From automated policy enforcement to built-in risk assessment tools, Azure transforms compliance into a streamlined, proactive process.
This guide explores how to align with GDPR, HIPAA, and SOC 2 using Azure security and compliance tools, while following data center security best practices and leveraging Azure Blueprint templates for faster implementation.
The Modern Compliance Landscape
Why Compliance is Getting More Complex
Most organizations don’t just need to comply with one framework. Instead, they navigate overlapping requirements like:
- GDPR for data protection in the EU
- HIPAA for healthcare data in the US
- SOC 2 for client trust and system integrity
Challenges that come with multi-framework compliance:
- Varying data classification needs
- Distinct audit and logging requirements
- Security controls that must satisfy multiple frameworks
- Ongoing monitoring, not one-time certification
Azure’s Unified Approach to Regulatory Compliance
Microsoft Azure simplifies multi-framework compliance by offering an integrated compliance platform with built-in governance.
Key Capabilities:
- Centralized Compliance Dashboard
Unified view for GDPR, HIPAA, SOC 2, and more - Azure Policy Compliance
Define, assign, and automatically enforce policies across subscriptions - Compliance Automation
Minimize manual errors through auto-generated reports and remediation flows - Risk Assessment Tools
Azure Security Center continuously evaluates and flags posture gaps
Implementing GDPR Compliance Using Azure
How to implement GDPR compliance in Azure:
To align with GDPR, Azure emphasizes data protection by design and by default, supported by automation, policy management, and layered access control.
Azure Policy Compliance Workflow:
- Define policies across resource groups
- Monitor compliance state
- Remediate non-compliant resources automatically
Key GDPR Controls Using Azure:
- Data residency enforcement via location-based policies
- Encryption mandates for data at rest and in transit
- RBAC and logging to secure and audit access
- Label-based classification with Azure Information Protection
Core Azure Tools for GDPR Alignment
Azure Information Protection (AIP)
- Automatic Classification based on content sensitivity
- Data Labeling and Protection with predefined and custom rules
- Access Controls including viewing, editing, copying, and printing restrictions
Technical Highlights:
- Supports 500+ file formats
- Deep integration with Microsoft 365 apps
- Regex-based classification rules
Azure Security Center
- Real-time security posture analysis
- GDPR-focused compliance dashboard
- Machine learning-driven threat detection
Integrated with:
Microsoft Threat Intelligence
Custom security recommendations
Compliance scoring based on control maturity
Steps for HIPAA Compliance Using Azure Security Center
HIPAA compliance requires tight control over Protected Health Information (PHI), supported by strong access control, encryption, and audit logging.
Azure Solutions for HIPAA:
- Azure Policy Templates tailored to HIPAA standards
- Azure Monitor Logs for detailed audit trails
- Key Vault and TDE for encryption and key lifecycle management
- Privileged Identity Management (PIM) to control admin access
- Multi-Factor Authentication (MFA) for user verification
These controls help meet the HIPAA Security Rule’s technical safeguards efficiently.
Azure Blueprint for SOC 2 Compliance
SOC 2 compliance focuses on security, availability, and confidentiality, especially for service organizations handling client data.
Azure offers Blueprint templates pre-mapped to SOC 2 controls, enabling faster, consistent setup across environments.
Blueprint Implementation Steps:
- Deploy SOC 2 Blueprint across subscriptions
- Assign built-in policies and initiatives
- Monitor through Azure Compliance Manager
- Remediate violations through policy-based automation
These templates enforce controls such as:
- Data encryption
- Role-based access
- Logging and incident response
- Secure configuration baselines
Implementing Data Protection Controls in Azure
Encryption Architecture:
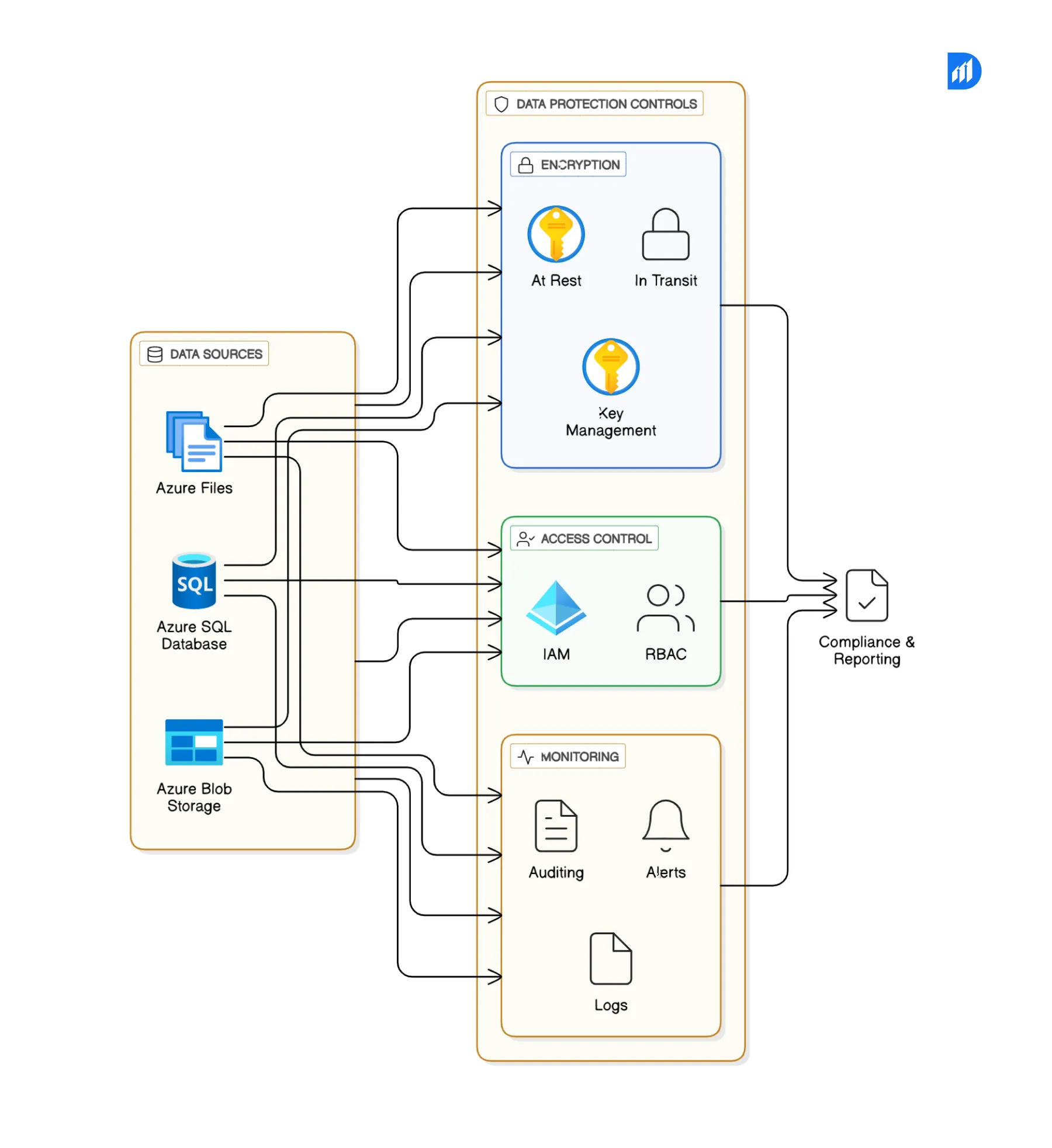
- Azure Key Vault for hardware-backed key storage
- Storage Service Encryption for Azure Blob, File, and Disk
- Transparent Data Encryption (TDE) for SQL databases
- Client-Side Encryption for high-sensitivity use cases
Identity & Access Management:
- Azure Active Directory for unified IAM
- Conditional Access for real-time risk mitigation
- Privileged Identity Management (PIM) for admin controls
- MFA to strengthen access beyond passwords
All of these form the foundation for data center security best practices within Azure.
Turning Compliance into a Strategic Advantage
With increasing scrutiny and evolving regulations, Azure security and compliance tools enable organizations to stay proactive.
By leveraging:
- Compliance automation
- Azure Blueprint templates
- Risk assessment tools
- Data protection controls
Businesses can shift compliance from a legal burden to a competitive differentiator.
Whether you’re navigating how to implement GDPR compliance in Azure, steps for HIPAA compliance using Azure Security Center, or leveraging an Azure Blueprint for SOC 2 compliance, Microsoft Azure helps organizations move faster, more securely, and with greater confidence.
Azure Security and Compliance: Your Guide to GDPR, HIPAA, and SOC 2 Implementation
When compliance feels overwhelming, Azure simplifies it.
Whether you’re dealing with healthcare regulations, privacy laws, or service audits, Microsoft Azure offers built-in frameworks, automation tools, and security layers to help you stay compliant, without slowing down your operations.
Let’s walk through how to align with GDPR, HIPAA, and SOC 2 using Azure security and compliance features, with practical implementation steps, best practices, and automation strategies.
HIPAA Compliance with Azure Security Center
HIPAA isn’t just about health data. It’s about protecting trust.
Azure Security Center helps you meet HIPAA’s required safeguards through layered controls.
Administrative Safeguards
- Security Officer Assignment: Define a responsible role for policy management.
- Training Protocols: Set up recurring security awareness programs.
- Access Management: Enforce minimum necessary access principles.
- Incident Response Plan: Document response procedures for PHI-related breaches.
Physical Safeguards
- Facility Controls: Use Azure’s compliant data centers with restricted physical access.
- Workstation Setup: Secure device configurations to avoid accidental exposure.
- Media Security: Control how storage devices are handled, transferred, or discarded.
- Device Access: Monitor and manage all portable device usage.
Technical Safeguards
- Access Control: Enforce unique user IDs and strong authentication.
- Audit Trails: Maintain detailed logging for all PHI access events.
- Data Integrity: Prevent unauthorized changes to sensitive health data.
- Encryption: Encrypt PHI both at rest and in transit.
Azure Blueprint Templates for HIPAA
Blueprints accelerate HIPAA alignment.
Key Components
- Blueprint Definition: Tailored compliance goals mapped to artifacts.
- Policy Artifacts:
- Built-in HIPAA-aligned Azure Policies
- Custom policies for unique organization needs
- Compliance scoring with visual dashboards
- Role Assignments:
- RBAC tailored for healthcare teams
- Least privilege principle enforced
- Logged role transitions
- Resource Templates:
- Security baselines pre-configured
- NSGs, encryption, and key vault setup
SOC 2 Compliance Using Azure Blueprints
SOC 2 is about trust. And trust is built through repeatable security practices.
Azure Blueprint for SOC 2 Maps to 5 Trust Criteria:
1. Security
- User authentication and authorization
- Ongoing risk assessments
- Change management workflows
- Continuous threat detection
2. Availability
- Azure Monitor and alerts for uptime
- Auto-backups and DR strategy
- Performance tuning for resilience
- Fast-track incident response
3. Processing Integrity
- Data accuracy controls
- Automated error flags
- Validation of inputs and processes
- Change approval workflows
4. Confidentiality
- RBAC and encryption controls
- Azure Key Vault for key management
- Encrypted communication protocols
- Role-based access to confidential data
5. Privacy
- Transparent data usage policies
- Retention and deletion processes
- Secure personal data disposal
GDPR Compliance on Azure
Data privacy isn’t optional, it’s your legal and ethical foundation.
How to Implement GDPR Compliance in Azure
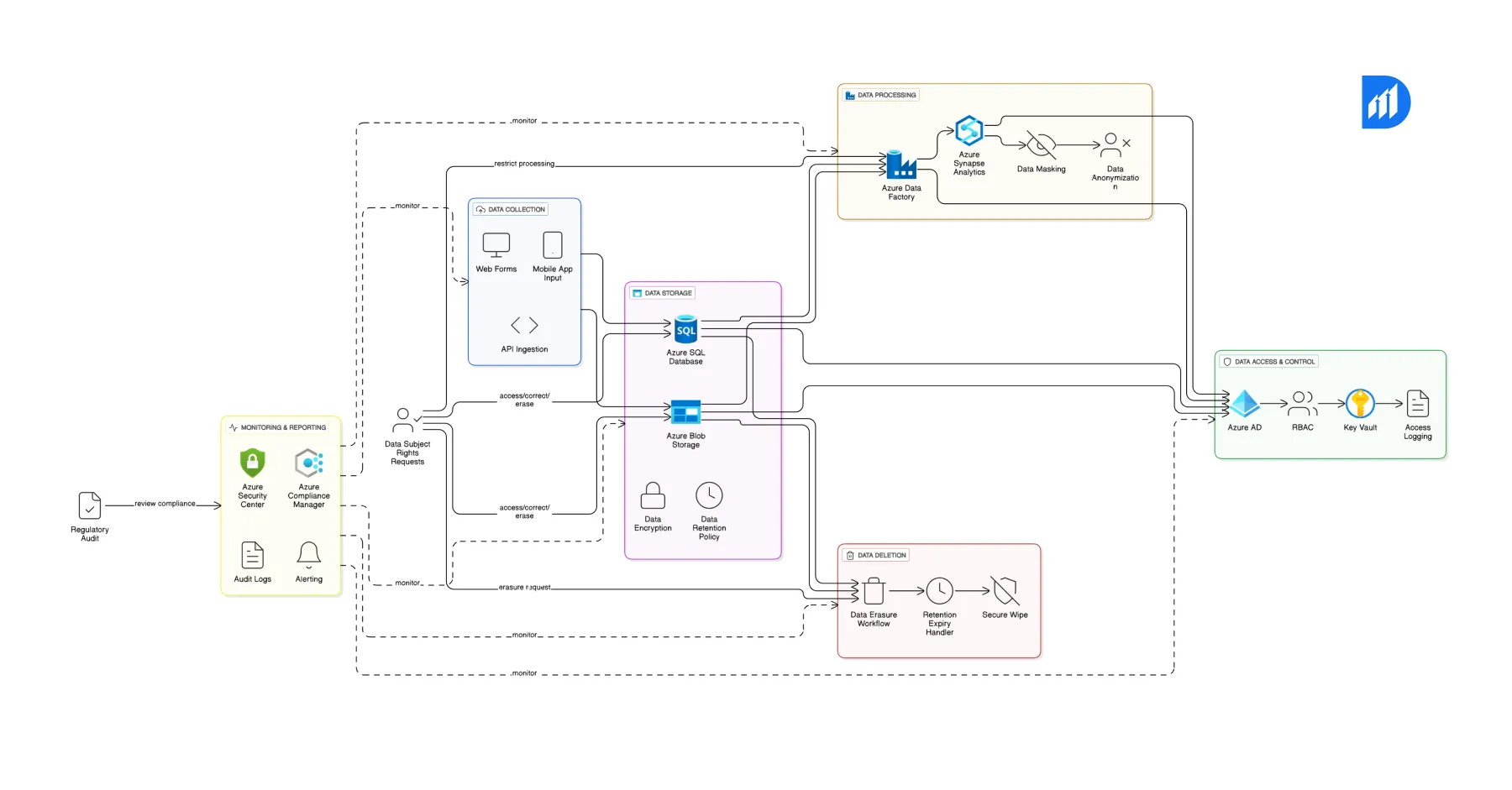
- Data Subject Rights: Configure tools to support right-to-access, erasure, and portability
- Data Location: Ensure data residency aligns with regional requirements
- Consent Management: Build consent workflows into app layers
- Data Mapping: Use Microsoft Purview for data discovery and classification
- Policy Enforcement: Apply Azure Policy compliance settings to restrict risky configurations
Azure Security Benchmark: Technical Controls for All Frameworks
Network Security
- Virtual Network segmentation
- NSGs and ASGs for traffic filtering
- Azure Firewall for central control
Identity and Access
- Azure AD for user and app authentication
- Conditional Access to adapt to real-time risk
- Privileged Identity Management (PIM) for admin control
- Use of service principals with scoped permissions
Data Protection Controls
- Azure Information Protection for data classification
- Encryption with customer-managed keys
- DLP (Data Loss Prevention) policies
- Geo-redundant backup and disaster recovery
Compliance Automation Strategies with Azure
Policy-as-Code
Azure lets you encode governance using Azure Policy.
Automated Remediation
- Azure Automation: Fix drift using scripts
- Logic Apps: Workflow-driven compliance
- Function Apps: Event-triggered remediations
- Event Grid: Real-time compliance responses
Risk Assessment and Continuous Monitoring
Use Azure-native Risk Assessment Tools:
- Asset inventory and threat modeling
- Continuous vulnerability scans
- Mitigation planning via Azure Secure Score
Tools to Leverage
- Azure Security Center Secure Score: Actionable insights with prioritization
- Microsoft Defender for Cloud: Cross-cloud compliance and threat protection
- Azure Sentinel: SIEM for real-time alerts and compliance reports
Data Center Security Best Practices
Physical Layer
- Biometric-based entry controls
- Environmental monitoring (humidity, power)
- 24/7 surveillance and incident detection
Network Layer
- Micro-segmentation using NSGs/ASGs
- Zero Trust Network Architecture
- Threat intelligence integrations
Application Layer
- Secure coding practices
- Static and dynamic code scanning
- Real-time vulnerability monitoring
Azure Compliance Implementation Roadmap
Phase 1: Foundation (Weeks 1–4)
- Subscription setup
- IAM configuration
- Baseline policy deployment
Phase 2: Frameworks (Weeks 5–12)
- GDPR, HIPAA, SOC 2 blueprint integration
- Monitoring configuration
- Alerting rules defined
Phase 3: Automation (Weeks 13–16)
- Compliance tasks automated
- Risk assessment tools implemented
- Custom policy development
Phase 4: Continuous Improvement (Ongoing)
- Review compliance dashboards
- Train teams regularly
- Adjust as regulations evolve
Final Word
Regulatory pressure isn’t going away. But with Azure security and compliance capabilities, staying ahead of evolving mandates is not only doable, it’s scalable.
By integrating compliance automation, data protection controls, and continuous risk assessment, you’re not just checking boxes. You’re building digital trust.
Ready to Act? Let’s simplify compliance together.
Durapid’s certified Azure consultants can help you:
- Implement GDPR, HIPAA, and SOC 2 with speed and precision
- Reduce compliance complexity
- Automate your audits and reporting
Book your Free Consultation and discover how to scale security with confidence.
Contact Us: Let’s build a secure, compliant, and resilient future.





